
I am sure at one-point or another, you’ve probably poked around in Office 365 Security and Compliance Center. There are a host of features waiting to be leveraged in this area: Advanced email tracing, Data Loss Prevention, Audit Log Search, Attack Simulation Training and more. While I plan on writing more about these individuals features (DLP in OneDrive for example), I want to focus on user activity auditing.
It doesn’t feel great to pry on user activity, but sometimes it is necessary to check for a multitude of reasons. The original place to do an Audit Log Search was at https://protection.office.com/unifiedauditlog. Microsoft has split this area into two different domains with differing services. There is some overlap, but they have different focuses. You can run an audit search in either of these newer areas:
https://security.microsoft.com/auditlogsearch
https://compliance.microsoft.com/auditlogsearch
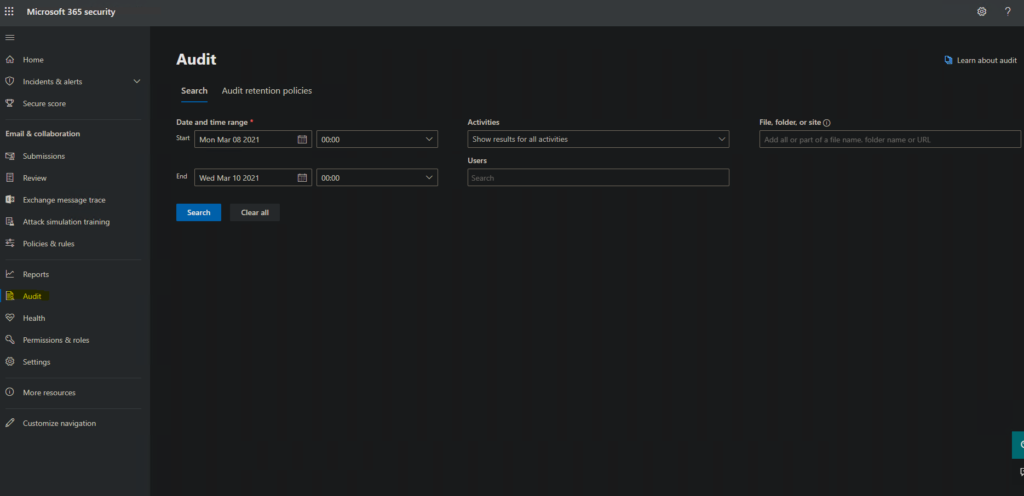
The User Interface for compliance and security center look identical. Set a date range and optional time, then select your user list and optional File, Folder or site.
The results are clean and the default columns provide good information. Each item can be expanded to view more information about each entry. You can also Export (download) the results by selecting the drop down arrow above the columns.
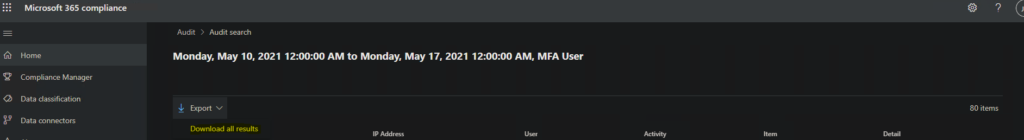
This already may be enough for you. Where I ran into issues was viewing the results from a laptop–which lead me to my old friend PowerShell. The cmdlet that we need is the Search-UnifiedAuditLog in the Exchange module. Microsoft does recommend using their Management Activity API for scripting this out, but this article isn’t going over API, CRUD or scripting activities.
You’ll want to setup a remote shell connection with Exchange Online. If you don’t have the commands handy, they are:
- Set-ExecutionPolicy RemoteSigned
- $UserCredential = Get-Credential
- $Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $UserCredential -Authentication Basic -AllowRedirection
- Import-PSSession $Session -DisableNameChecking
- Bear in mind, basic authentication will eventually be deprecated and Exchange Online PowerShell V2 will be the standard. Also, basic authentication does not work with MFA enabled accounts.
There are a lot of possibilities with the Search-UnifiedAuditLog cmdlet. If you don’t feel like reading the entire help page (And why should you? That’s why you’re here), and you are looking for ACTIONABLE events of a user, I recommend working from this command template.
Search-UnifiedAuditLog -UserIds "user@emailaddress" -StartDate "a/start/date" -EndDate "an/end/date" -Formatted -ResultSize "2000" -Operations "FileCopied","FileDeleted","FileDeletedFirstStageRecycleBin","FileDeletedSecondStageRecycleBin","FileDownloaded","FileModified","FileMoved","SearchQueryPerformed","FileRenamed" | select ResultIndex,UserIds,Operations,AuditData,IsValidNow, this command is ugly. I know. I get it. However, this gets the information into your shell. You can save this as a variable and use a parser to lookup for specific information. You can export this to a csv file–whatever you can do in PowerShell. For now, let’s break the syntax down a bit.
First parameter is the username or comma separated usernames you want to look up. Second and third parameter are beginning and end date dates. The -Formatted parameter is pretty crucial. If you don’t include that parameter, the Audit Data column/field will come back almost unreadable. ResultSize is up to you, I did 2000 as a placeholder. Operations are the actions that the user(s) took: Delete a file, Delete from second stage recycle bin, Access a file, Rename a file, etc. You do not have to use what I put there. There are a slew of options on this section of the website https://docs.microsoft.com/en-us/microsoft-365/compliance/search-the-audit-log-in-security-and-compliance?view=o365-worldwide#file-and-page-activities. Finally, I’ve filtered the view with the Select-Object cmdlet to show ResultIndex, UserIds, Operations, AuditData and IsValid.
If you want to export this to a csv file, you only need to pass it through to one more command.
Export-Csv -NoTypeInformation -Encoding UTF8 -Path C:\Users\you\anywhereyouwant\filename.csvSo the final command with the export will look like:
Search-UnifiedAuditLog -UserIds "user@emailaddress" -StartDate "a/start/date" -EndDate "an/end/date" -Formatted -ResultSize "2000" -Operations "FileCopied","FileDeleted","FileDeletedFirstStageRecycleBin","FileDeletedSecondStageRecycleBin","FileDownloaded","FileModified","FileMoved","SearchQueryPerformed","FileRenamed" | select ResultIndex,UserIds,Operations,AuditData,IsValid | Export-Csv -NoTypeInformation -Encoding UTF8 -Path c:\you\anywhereyouwant\filename.csvThanks for reading and feel free to message me with any ideas for further articles or videos.